Program Blocks Websites Temporarily
Program Blocks Websites Temporarily' title='Program Blocks Websites Temporarily' />
 DDOS Program Denial Of Service Attack. A Denial of Service Do. S or distributed denial of service DDo. S attack is a deliberate attempt to prevent legitimate users of a machine or network from accessing its resources. The means of carrying out these kinds of attacks, the motive behind them and their targets vary, but. Generally, the attacks involve efforts to indefinitely or temporarily suspend or interrupt the services of a host computer connected to the Internet. For those not ready to go whole hog on their Internet deprivation, Stutzman also sells a 15 program called AntiSocial that blocks distracting social. By definition, DDo. S attacks are perpetrated by two or more users or bots while Do. S attacks are sent by a single person or system but these terms are often used interchangeably. A DDo. S attacker typically uses your computer to attack another one. As of July 2. 01. Do. S attacks has gone up to an all time high of an average 2. A DDo. S attack typically involves a cracker using a network of zombie bot computers to sabotage a certain specific website or server. The cracker tells all the bot computers on his botnet to contact the server or website repeatedly andconsistently. This sudden increase in server traffic results in the site loading very slowly for its legitimate users, or even shut down completely is the requests overwhelm its resources. Some tricky botnets may use uncorrupted bot computers as part of the DDo. S attack. The cracker sends a command that initiates this attack to his zombie army of computers. Each of them then sends a connection request to another innocent computer known as a reflector. Block-a-Website-on-Your-Computer-Step-2-Version-4.jpg/aid1001668-v4-728px-Block-a-Website-on-Your-Computer-Step-2-Version-4.jpg' alt='Program Blocks Websites Temporarily' title='Program Blocks Websites Temporarily' />Focus Better and Get More Done. FocalFilter is a free productivity tool that helps you focus by temporarily blocking distracting websites. After the block timer runs. If you are new to building niche websites or even if you are more experienced, you are probably interested in seeing some specific examples of successful niche. Highlands resident Dwight Chandler, who lives near the flooded Highlands Acid Pit, examines his flooddamaged home. Photo AP After a week of storms and. The latest update to the Xbox Ones dashboard is rolling out to preview program alpha members today, adding cool new features like a modernized community page, a. Garcinia Blocks Fat Dr Oz Com Forskolin Weight Loss Program Who Sells Forskolin For Weight Loss Forskolin Comparison. Plane Games For Boys. Cold Turkey is a free productivity program that you can use to temporarily block distractions so that you can get your work done
DDOS Program Denial Of Service Attack. A Denial of Service Do. S or distributed denial of service DDo. S attack is a deliberate attempt to prevent legitimate users of a machine or network from accessing its resources. The means of carrying out these kinds of attacks, the motive behind them and their targets vary, but. Generally, the attacks involve efforts to indefinitely or temporarily suspend or interrupt the services of a host computer connected to the Internet. For those not ready to go whole hog on their Internet deprivation, Stutzman also sells a 15 program called AntiSocial that blocks distracting social. By definition, DDo. S attacks are perpetrated by two or more users or bots while Do. S attacks are sent by a single person or system but these terms are often used interchangeably. A DDo. S attacker typically uses your computer to attack another one. As of July 2. 01. Do. S attacks has gone up to an all time high of an average 2. A DDo. S attack typically involves a cracker using a network of zombie bot computers to sabotage a certain specific website or server. The cracker tells all the bot computers on his botnet to contact the server or website repeatedly andconsistently. This sudden increase in server traffic results in the site loading very slowly for its legitimate users, or even shut down completely is the requests overwhelm its resources. Some tricky botnets may use uncorrupted bot computers as part of the DDo. S attack. The cracker sends a command that initiates this attack to his zombie army of computers. Each of them then sends a connection request to another innocent computer known as a reflector. Block-a-Website-on-Your-Computer-Step-2-Version-4.jpg/aid1001668-v4-728px-Block-a-Website-on-Your-Computer-Step-2-Version-4.jpg' alt='Program Blocks Websites Temporarily' title='Program Blocks Websites Temporarily' />Focus Better and Get More Done. FocalFilter is a free productivity tool that helps you focus by temporarily blocking distracting websites. After the block timer runs. If you are new to building niche websites or even if you are more experienced, you are probably interested in seeing some specific examples of successful niche. Highlands resident Dwight Chandler, who lives near the flooded Highlands Acid Pit, examines his flooddamaged home. Photo AP After a week of storms and. The latest update to the Xbox Ones dashboard is rolling out to preview program alpha members today, adding cool new features like a modernized community page, a. Garcinia Blocks Fat Dr Oz Com Forskolin Weight Loss Program Who Sells Forskolin For Weight Loss Forskolin Comparison. Plane Games For Boys. Cold Turkey is a free productivity program that you can use to temporarily block distractions so that you can get your work done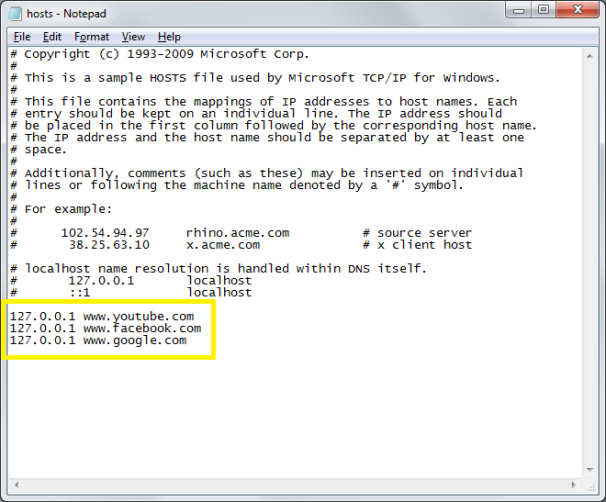 This request appears to the reflector as if it originates from a targeted victim of the attack and not from the zombie army. The reflectors bombard the victim system with information, eventually making its performance to suffer or causing it to shut down completely because of the inundation with a myriad of unsolicited responses from multiple computers at once. In the victims perspective, it appears that the reflectors attacked its system while in the reflectorsperspective it seems like the victim requested those packets of information, an intelligent ploy that ensures that the zombies remain hidden, with the cracker himself being even more out of sight Some of the most common types of DDo. S names include Ping of Death here, bot computers create huge packets of information and send them on to victim systems. Mailbomb this involves the the bombardment of e mail servers with a massive amount of e mail traffic that often leads to their crashing. Smurf Attack here, bots send ICMP or lnternet Control Message Protocol messages to reflectors, which then attack a targeted victim system. Teardrop pieces of an illegitimate information packet are sent to a victim system by an army of bots. When the system tries to recombine these pieces to make a packet, it crashes. Other types of Do. S and DDo. S attacks include SYN floods, Slow Read, Peer to Peer and R U Dead Yet RUDY attacks. Some major technology, software, computer security and Internet companies have been. DDo. S attack victims including Microsoft which suffered a DDo. S attack called My. Doom. Others include Amazon, Yahoo, CNN and e. Bay. Once an army of bots commences a DDo. S attack against a targeted victim, there are a few measures the system administrator could do to prevent a catastrophe. For instance, he could limit the amount of traffic that is allowed on his server. Though this technique also restricts legitimate connections, it is a step towards preventing more damage. An administrator could also try to determine the origin of an attack and try filtering the traffic. Unfortunately, this is not always an easy thing to do iven that many zombie computers will disguise or spoof their addresses to cover their tracks.
This request appears to the reflector as if it originates from a targeted victim of the attack and not from the zombie army. The reflectors bombard the victim system with information, eventually making its performance to suffer or causing it to shut down completely because of the inundation with a myriad of unsolicited responses from multiple computers at once. In the victims perspective, it appears that the reflectors attacked its system while in the reflectorsperspective it seems like the victim requested those packets of information, an intelligent ploy that ensures that the zombies remain hidden, with the cracker himself being even more out of sight Some of the most common types of DDo. S names include Ping of Death here, bot computers create huge packets of information and send them on to victim systems. Mailbomb this involves the the bombardment of e mail servers with a massive amount of e mail traffic that often leads to their crashing. Smurf Attack here, bots send ICMP or lnternet Control Message Protocol messages to reflectors, which then attack a targeted victim system. Teardrop pieces of an illegitimate information packet are sent to a victim system by an army of bots. When the system tries to recombine these pieces to make a packet, it crashes. Other types of Do. S and DDo. S attacks include SYN floods, Slow Read, Peer to Peer and R U Dead Yet RUDY attacks. Some major technology, software, computer security and Internet companies have been. DDo. S attack victims including Microsoft which suffered a DDo. S attack called My. Doom. Others include Amazon, Yahoo, CNN and e. Bay. Once an army of bots commences a DDo. S attack against a targeted victim, there are a few measures the system administrator could do to prevent a catastrophe. For instance, he could limit the amount of traffic that is allowed on his server. Though this technique also restricts legitimate connections, it is a step towards preventing more damage. An administrator could also try to determine the origin of an attack and try filtering the traffic. Unfortunately, this is not always an easy thing to do iven that many zombie computers will disguise or spoof their addresses to cover their tracks.